Encryption Intelligence
Ampliphae Encryption Intelligence enables you to gain complete visibility into all encryption technologies deployed across the organisation.
Inventory: By providing a comprehensive view of encryption across the organization, Encryption Intelligence helps to eliminate blind spots and proactively identify areas that require attention.
Eliminate Weak Points: With Encryption Inelligence, quickly identify where encryption is weak and vulnerable to attack, so you can take prompt action to strengthen security posture.
Improve Security: Improve overall security and reduce the risk of data breaches and other cyber threats.
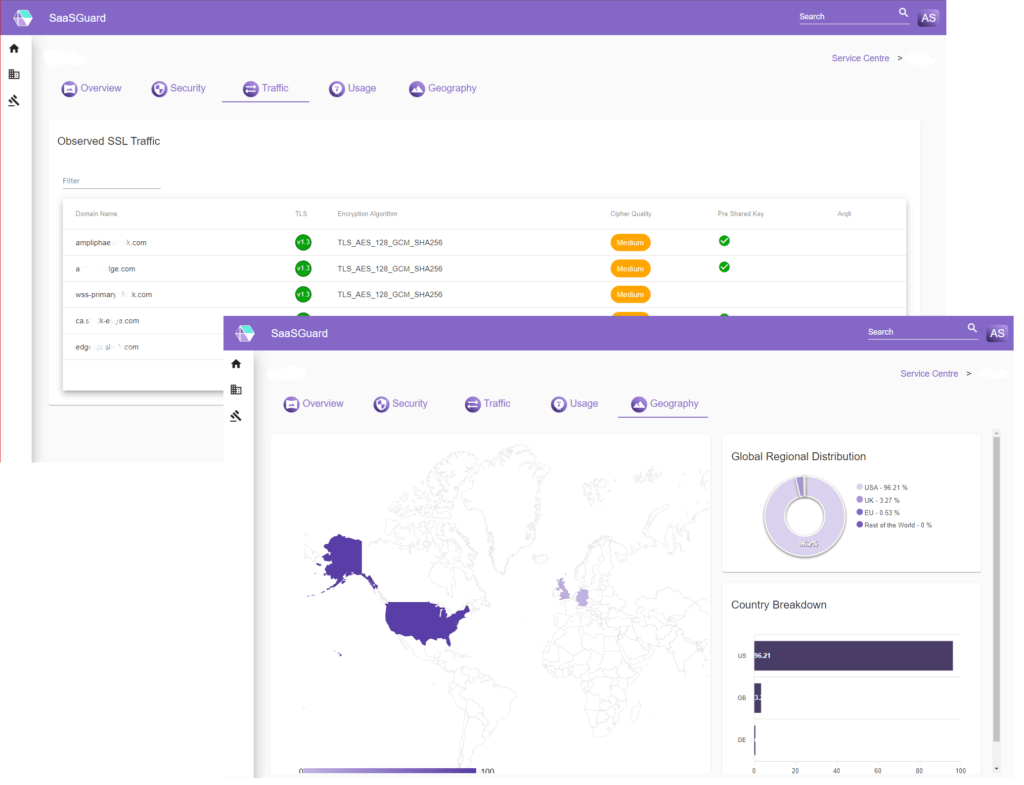
Ensure encryption technology is up-to-date and effective so that your sensitive data is protected
Read the full datasheet here!
90%
of IoT network traffic is unencrypted
49%
of websites still support TLS 1.0 or TLS 1.1
80%
of Cloud application traffic crosses national borders
The Quantum Threat
Quantum computers will render current encryption schemes obsolete, putting sensitive data at risk.
Security analysts are scrambling to find solutions to this unprecedented threat, searching for new ways of protecting sensitive data that are not vulnerable to quantum computers.
Ampliphae Encryption Intelligence encryption analytics helps you locate weak encryption schemes that are vulnerable to Quantum Attack before your data is compromised.

Can you identify....
Vendors
Do you know every party in your data and application supply chain?
Locations
Do you know where in the world all your critical application traffic goes?
Ciphers
Do you know which applications use sub-standard encryption?
Automatically build a trusted Encryption Inventory
Discover
New applications and vendor connections as they are used.
Understand
How your application data is protected through detailed traffic analysis.
Detect
Uncover all the weak encryption schemes in use across the organisation
Respond
Understand which insecure applications are used to support your business – and address the risks
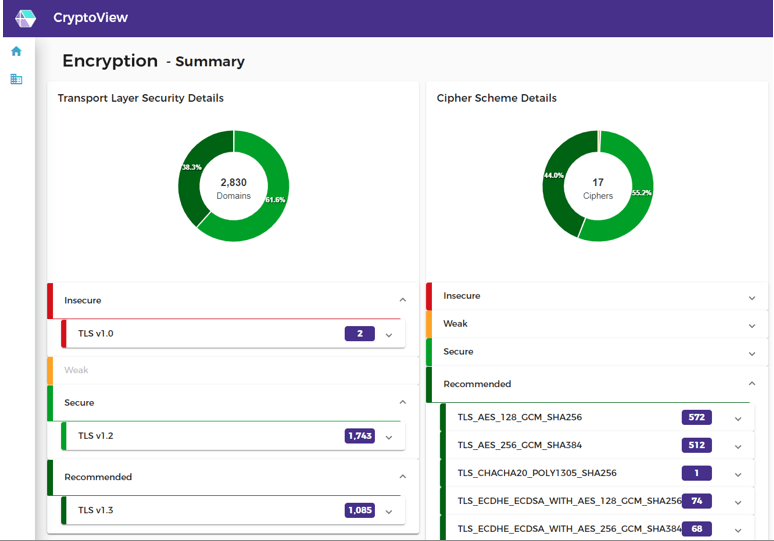
Automatically identify applications with specific vulnerabilities
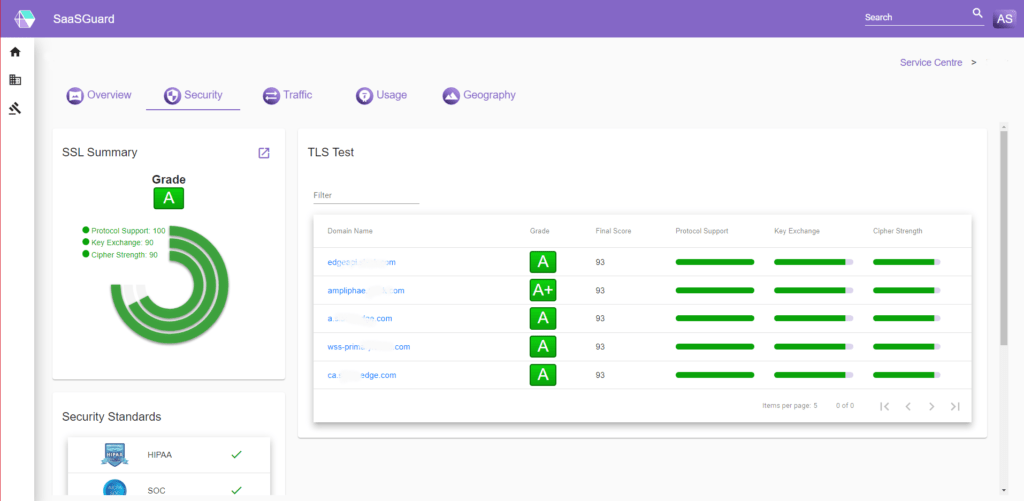
Identify
Identify SaaS and in-house applications which contain critical data
Find
Find applications that are exposed to known cyber security vulnerabilities
Understand
Identify the security and compliance implications of communication vulnerabilities
Respond
Address vulnerabilities through technical and commercial mitigations
Automatically assess the security capabilities of your supply chain
Discover
Build an inventory of all the SaaS that your existing processes don’t know about.
Locate
Understand where in the world the SaaS vendor processes your data
Assess
Decide whether the security protections and certifications used by a vendor are sufficient
Respond
Prevent your people putting themselves and your data at risk by accessing insecure applications